Bot Attacks: Types and
Mitigation Strategies
What is a bot attack?
Bot attacks are a form of automated attacks that take place online. They are carried out by automated scripts or software programs called bots.
Here, it’s important to note that there are two basic types of bots. There are good bots designed to streamline daily tasks for humans, like chatbots, for example.
On the other side, there are bad bots used for bot attacks which cause harm to businesses and individuals online.
These bad bots are used for a variety of malicious tasks, including stealing data, overwhelming website traffic, skewing website data and analytics, spreading spam, or repetitively clicking on online ads to deplete ad budgets.
What’s even more worrying in the cyber world is that these malicious bot attacks experienced an enormous 112% year-over-year increase in 2022. These attacks pose significant risks, not only in terms of financial losses but also in terms of reputational damage.
Why businesses should be concerned
about bot attacks?
Here are some statistics and harmful effects caused by bot attacks in the recent years:
- A report by Enisa showed that 60% of malicious bot activity is associated with stealing user credentials (source).
- Clickjacking attacks grew by 125% in 2022 only (source).
- Scalper bots attacked Ticketmaster’s servers in November 2022 and caused chaos with Taylor Swift’s tour ticket sales (source).
- By region, Latin America saw the largest year-over-year increase in automated bot attack volume in 2021, with over 450% (source).
Annual Business Losses
to Bot Attacks

How do bot attacks work?
At their core, bot attacks leverage the power of automation. Cybercriminals, or hackers, create bots to execute specific actions at a scale. They define these actions based on their objectives, translate them into code, and form the scheme bots follow.
Bots, in turn, operate in strict accordance with the provided scheme. Typically, they begin by identifying or locating their designated target. This target can include a variety of entities, including websites (sometimes specific sections of a website), business systems, networks, online advertisements, servers, APIs, and other endpoints.
Once locked onto their target, bots execute their assigned tasks at high speed and with precision, mimicking human behavior, which makes them hard to detect.
Block bot attacks within minutes
Single bot attack vs.
botnet attacks
There can be a single bot attack or multiple bot attacks conducted by several bots grouped together, also known as botnet attacks.
A single bot attack is carried out by one bot, acting independently. These attacks often involve relatively straightforward tasks and are typically employed for simpler, less sophisticated attacks. For example, bots can be used for comment spamming, scraping websites, or credential stuffing.
On the other hand, a botnet attack involves a network of bots deployed across multiple compromised devices working collectively to carry out malicious activities.
Common uses of botnets include launching Distributed Denial of Service (DDoS) attacks, sending out spam emails, distributing malware, and conducting large-scale attacks on websites or networks.
Read this article to learn more about botnet attacks and how to block them.
What are the different types of bot attacks?
Bot attacks come in various forms, each tailored to achieve different malicious objectives.
Understanding these different types is essential for recognizing potential
threats and implementing effective defense mechanisms.
Here are some of the most common types of bot attacks:
Distributed Denial of Service (DDoS) attacks
DDoS attacks primarily target websites, networks, or servers. They aim to disrupt their operations by overwhelming them with massive traffic volumes.
Cybercriminals use DDoS bots to flood their target with many server requests or messages all at once. The surge of requests overwhelms the targeted website or service, causing it to slow down or crash. As a result, it can’t respond to legitimate requests from regular users, and eventually, they’ll leave.
Consequently, DDoS attacks have the potential to temporarily disrupt or even shut down websites or online services, making businesses lose real traffic and customers.
Click fraud & ad fraud
Click fraud and ad fraud involve the use of click bots to mimic online interactions, such as clicks, impressions, or conversions.
These bots trick advertising platforms and businesses by generating fake interactions, giving the illusion of real user engagement. Their primary aim is to inflate click rates for various purposes.
These purposes may include draining competitors’ ad budgets, boosting website search rankings unfairly, or generating revenue through ads on fraudulent websites or apps. As a result, advertisers waste their budgets on non-genuine interactions, reducing the efficiency of both the ad campaigns and advertising platforms.
Web scraping
Web scraping bot attacks involve unauthorized bots extracting data from a website, including texts, images, and personal or payment information.
The motivations behind such attacks can vary. Some attackers may aim to replicate your business strategies to gain a competitive advantage, while others might exploit the stolen data to impersonate your business and spread false information.
In more malicious cases, they may target your users’ personal information and financial details, leading to potential identity theft or the illegal sale of this data on the dark web.
Scalper attacks
Scalper bots are used to purchase large numbers of various high-demand products, with the goal of later selling them at much higher prices.
These attacks are most common in ticket sales, like concerts and sports events (“ticketing attacks”), but also occur during major retail events such as Black Friday. E-commerce sites and limited-edition items are common targets.
This malicious practice raises prices and makes it more difficult for genuine users to find the products they’re interested in.
Spam attacks
Spam attacks are the practice of sending unsolicited and unwanted digital communications, such as emails, text messages, or social media posts, in bulk.
These attacks can take many forms, including email spam, social media spam, and comment spam on websites.
The goal of spam bots is typically to promote unwanted products or services, spread malware, or gather personal information.
Credential stuffing and
Account takeover (ATO)
Credential stuffing is a type of bot attack where cybercriminals use automated bots to test stolen username and password combinations across various online platforms.
They rely on the fact that many people reuse passwords for multiple accounts.
Successful credential stuffing often leads to account takeover (ATO). This happens when cybercriminals gain control of a user’s account on a website, app, or service.
Once they have access, they can carry out various malicious actions, such as stealing personal information, making unauthorized purchases, or spreading spam.

CHEQ against
bot attacks
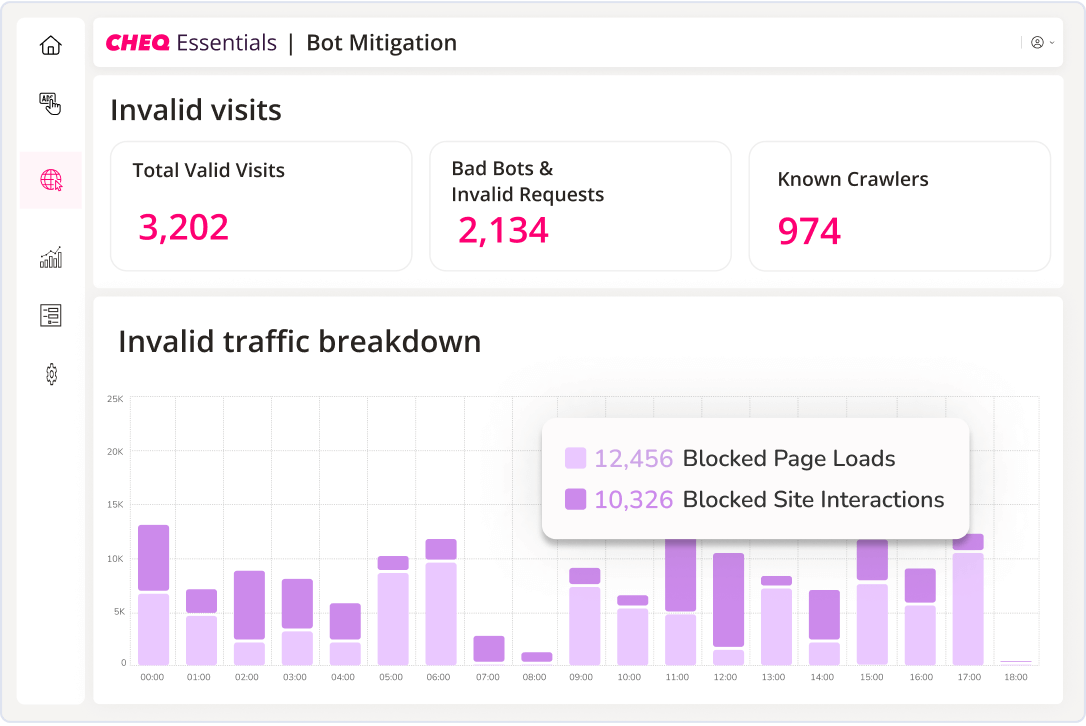
CHEQ Essentials is the leading cybersecurity solution focused on fighting bad bots across the internet.
Its purpose is to help businesses like yours protect your website and marketing budgets and receive real, human traffic only. Our solution does this by continually monitoring both organic, direct, and paid traffic to identify and block malicious activities such as fraudulent clicks on Google Ads, Microsoft Ads, and Facebook Ads.
With comprehensive reporting, it provides you with insights into your fraud risks and how it is being managed.
CHEQ Essentials uses advanced technology to conduct more than 2,000 real-time browser tests to detect any visitors trying to hide their identity. This ensures that no genuine traffic is accidentally blocked.
Frequently asked questions
What is a bot in cybercrime?
Bots are software codes or scripts programmed to execute specific tasks over the internet. When it comes to cybercrime, the tasks that these bots perform are with malicious intent.
Such malicious and fraudulent actions cause serious harm to businesses online. They can hurt the regular operations of websites, systems, marketing activities, etc., resulting in ineffective marketing campaigns, poor business decisions based on irregular data, financial losses, and more.
Bots are a major threat to cybersecurity, and they are becoming increasingly sophisticated and difficult to detect. Therefore, organizations need to implement strong security measures to protect themselves from bot attacks.
How to recognize a bot attack?
Usually, a bot attack would slow down your website, network, or system. So, if you notice an unusual change in the way they commonly work, it can be taken as a red flag and investigated further.
Google Analytics or other reporting tools should be your first go-to tool. Dig deeper into your analytics to spot uncommon patterns, such as website visits coming from strange locations, repetitive clicks from the same user or IP address, high bounce rates, etc.
Remember to regularly monitor your traffic and keep your protection measures up to date.
Read this bot protection guide to learn some commonly used techniques and strategies to minimize the risks of bot attacks.
How can bot mitigation improve my performance?
Bot mitigation improves performance by preventing malicious bots from engaging with your pages and forms, ensuring genuine user access, faster load times, and a positive user experience. It not only prevents bot attacks but also safeguards against fraud, maintains data integrity, and contributes to server efficiency, reducing the risk of downtime.
Can CHEQ Essentials block bot traffic from my website?
Yes, CHEQ Essentials’ bot mitigation solution can keep your website protected from malicious bot activity.
It uses a combination of advanced algorithms to analyze patterns and detect fraudulent activity. By constantly monitoring suspicious activity, it detects and blocks malicious bots from interacting with your website in real time.
This way, the invalid traffic stays filtered out from your website, allowing you to focus on genuine interactions and improve website performance for real users.
Can CHEQ Essentials help me achieve better ROI for my campaigns?
Yes, it can. CHEQ Essentials’ paid marketing protection blocks fraudulent interactions from your ads, saving you money and reducing wasted ad spend.
Additionally, your ads will only be seen and clicked by real people with genuine interest, increasing the likelihood of conversions and purchases.
Finally, CHEQ Essentials ensures that your pipeline is filled with only real leads, further boosting your ROI.
